Control access to tools
Configure the Agent Gateway to require a JWT token to authenticate requests and use an RBAC policy to authorize access to tools for JWT tokens that contain specific claims.
Configure the Agent Gateway
-
Download a sample, local JWT public key file. You use this file to validate JWTs later.
curl -o pub-key https://raw.githubusercontent.com/agentgateway/agentgateway/refs/heads/main/manifests/jwt/pub-key -
Create a configuration file for your Agent Gateway. In this example, you configure the following elements:
- Listener: An SSE listener that listens for incoming traffic on port 3000. The listener requires a JWT to be present in an
Authorizationheader. You use the local JWT public key file to validate the JWT. Only JWTs that include thesub: meclaim can authenticate with the Agent Gateway successfully. If the request has a JWT that does not include this claim, the request is denied. - RBAC policy: An RBAC policy that allows access to the
everything_echotool when a JWT token with thesub: meclaim is present in the request. - Target: The Agent Gateway targets a sample, open source MCP test server,
server-everything.
cat <<EOF > ./config.json { "type": "static", "listeners": [ { "name": "sse", "protocol": "MCP", "sse": { "address": "[::]", "port": 3000, "authn": { "jwt": { "issuer": [ "me" ], "audience": [ "me.com" ], "local_jwks": { "file_path": "./pub-key" } } }, "rbac": [ { "name": "default", "rules": [ { "key": "sub", "value": "me", "resource": { "type": "TOOL", "target": "everything", "id": "echo" }, "matcher": "EQUALS" } ] } ] } } ], "targets": { "mcp": [ { "name": "everything", "stdio": { "cmd": "npx", "args": [ "@modelcontextprotocol/server-everything" ] } } ] } } EOF - Listener: An SSE listener that listens for incoming traffic on port 3000. The listener requires a JWT to be present in an
-
Run the Agent Gateway.
agentgateway -f config.json
Verify access to tools
-
Open the Agent Gateway UI to view your listener and target configuration.
-
Connect to the MCP server with the Agent Gateway UI playground.
-
Go to the Agent Gateway UI Playground.
-
In the Connection Settings card, select your Listener Endpoint.
-
In the Bearer Token field, enter the following JWT token. The JWT token includes the
sub: meclaim that is allowed access to theeverything_echotool.eyJhbGciOiJFUzI1NiIsImtpZCI6IlhoTzA2eDhKaldIMXd3a1dreWVFVXhzb29HRVdvRWRpZEVwd3lkX2htdUkiLCJ0eXAiOiJKV1QifQ.eyJhdWQiOiJtZS5jb20iLCJleHAiOjE5MDA2NTAyOTQsImlhdCI6MTc0Mjg2OTUxNywiaXNzIjoibWUiLCJqdGkiOiI3MDViYjM4MTNjN2Q3NDhlYjAyNzc5MjViZGExMjJhZmY5ZDBmYzE1MDNiOGY3YzFmY2I1NDc3MmRiZThkM2ZhIiwibmJmIjoxNzQyODY5NTE3LCJzdWIiOiJtZSJ9.cLeIaiWWMNuNlY92RiCV3k7mScNEvcVCY0WbfNWIvRFMOn_I3v-oqFhRDKapooJZLWeiNldOb8-PL4DIrBqmIQ -
Click Connect. The Agent Gateway UI connects to the target that you configured and retrieves the tools that are exposed on the target.
-
Verify that you see a list of Available Tools.
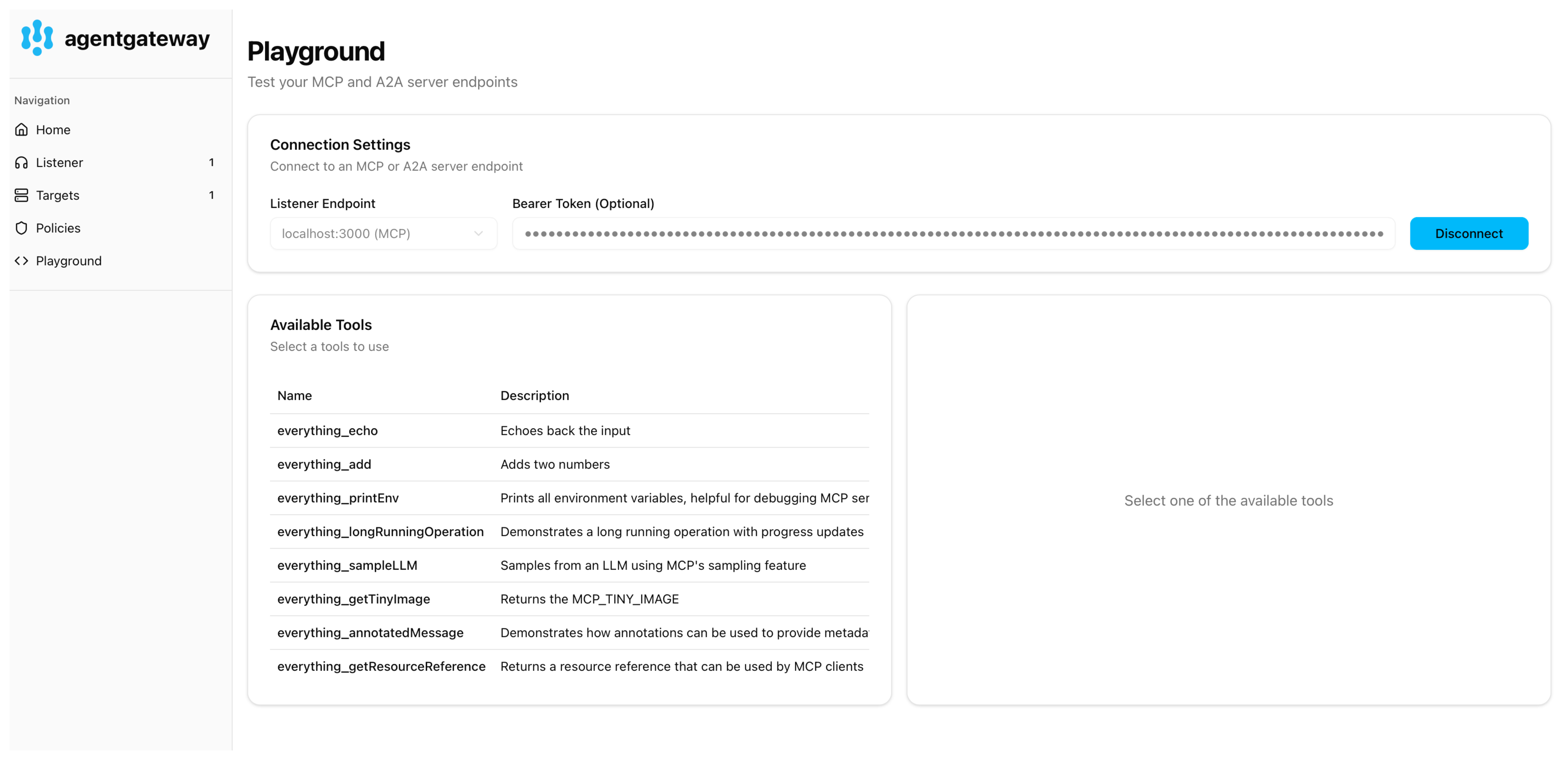
-
-
Try out access to the tools.
- Select the
everything_echotool, enter any string in the message field, such ashello world, and click Run Tool. Verify that access to the tool is granted and that you see your message echoed.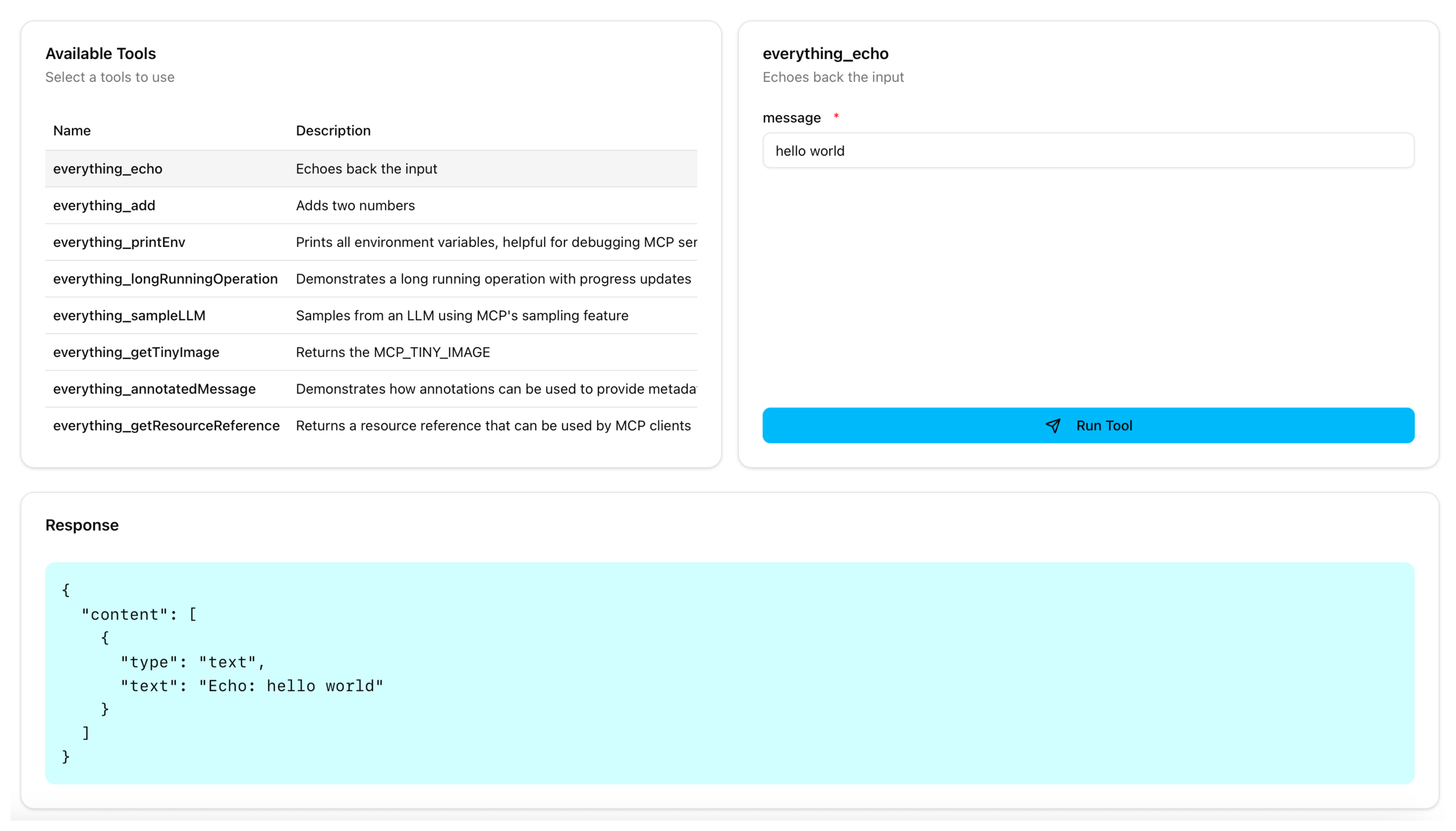
- Select a different tool, such as
everything_add, enter any number in the a and b fields, and click Run Tool. Verify that access to the tool is denied, because the RBAC policy only allowed access to theeverything_echotool.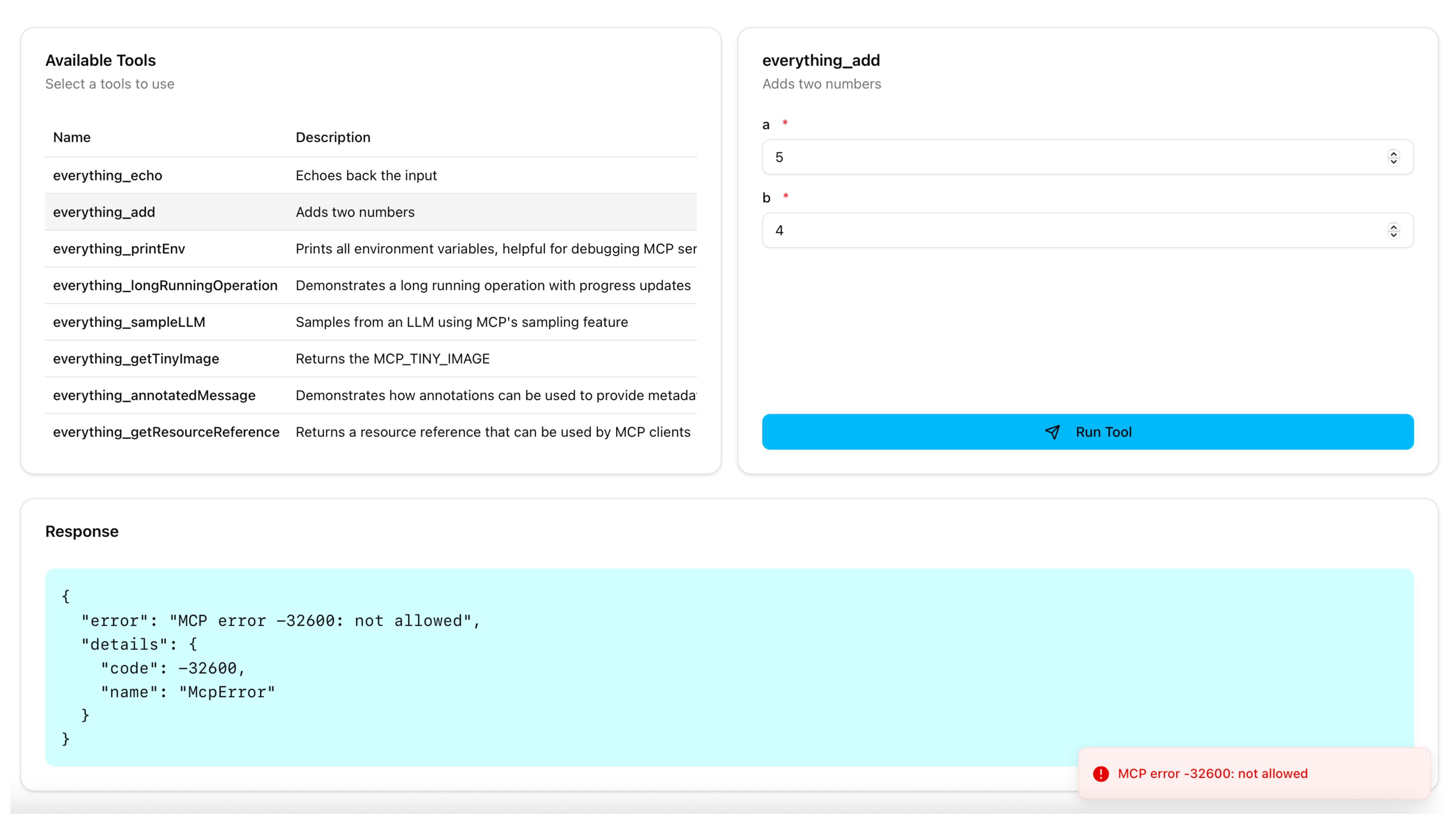
- Select the